I only react now about this vulnerability famous from the past few days, in order to have more feedback before talking about it.
Introduction
The piece of code introducing this vulnerability was introduced with OpenSSL 1.0.1 on 14th march 2012, and was discovered by Google and Codenomicon in April 2014.The impacted version are: OpenSSL 1.0.1 (included) to 1.0.1f (included).
A lot of news talk about the average citizen but how about the companies and the IT Pro? Indeed some famous products likes VMWare and Oracle used OpenSSL and are impacted by the vulnerability.
However Microsoft solutions used their own implementation of TLS/SSL with Schannel and are not vulnerable: AZURE, Office 365, ...
Clearly most of the attacks will be social engineering if a company use FaceBook for example, or others attacks on the critical data stored in databases or in virtual machines.
How it works
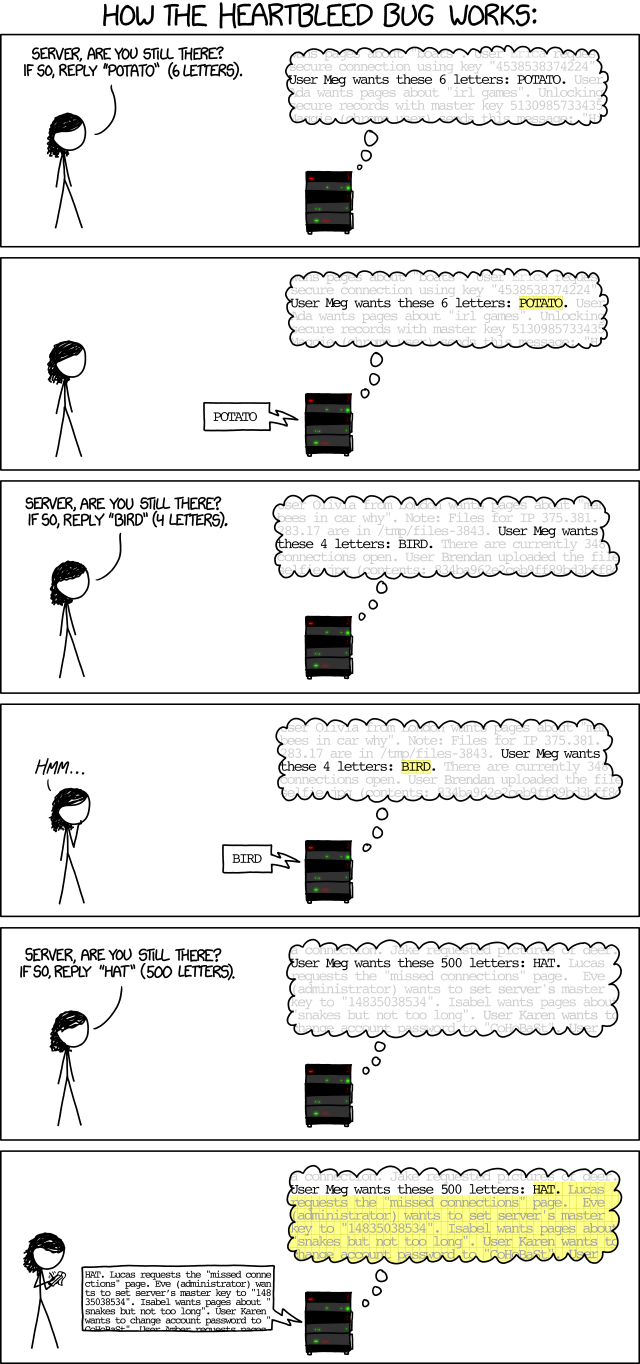
RFC6520 describe the heartbeat functionality for TLS, which allow to an endpoint to ask for a heartbeat message to the other sides. On the vulnerable version it's possible to send a modified payload in order to request a bigger than expected in order to dump the active memory (64ko maximum) of the server, which contain TLS sessions and critical data like:- Credit card number
- Passwords
- Server private key
But keeps in mind that the attacker will randomly look for a lot amount of data in order to found the right useful information, which could take time.
Preventives actions
Some editors react quickly:- Update OpenSSL or build again your actual version with the -DOPENSSL_NO_HEARTBEATS in order to disable the heartbeat functionality
- Update your VMWare servers: http://www.vmware.com/security/advisories/VMSA-2014-0004.html
- Update your Oracle databases: http://www.oracle.com/technetwork/topics/security/opensslheartbleedcve-2014-0160-2188454.html
- If your are lucky and got F5, use protecting rules: https://f5.com/solutions/mitigation/mitigating-openssl-heartbleed
More about this
If you want to know more:- Dedicated website: http://heartbleed.com/
- Wikipedia article: http://en.wikipedia.org/wiki/Heartbleed
- Main sites status: http://www.lwgconsulting.com/news/sites_affected_by_heartbleed_bug.aspx
- Testing tools for Internet exposed resources: https://filippo.io/Heartbleed
Thanks to Maxime Rastello for the review of the article.



Aucun commentaire:
Enregistrer un commentaire